Network security begins with asset discovery – the process by which an organization keeps track of all authorized and unauthorized devices and software connected to the company network.
After asset discovery, IT can implement asset management, including tracking and correcting authorized devices and software. They can also deny access to unauthorized and unmanaged accounts, as well as prevent unapproved software from being installed on network devices.
Asset discovery and management are important preventative measures for cybersecurity, leading to decreased costs, decreased risk, and increased business performance.
So why doesn’t every company have a robust asset management program?
In short, because it requires priority, budget, and process.

Asset Management – Barriers to Implementation
Asset management is often time-consuming and difficult. All too frequently, there is no true, accurate account of assets connected to the network, making asset management arduous and leaving an organization open to attack.
IT organizations struggle with asset management for the following reasons:
Priority
Asset management is not sexy, fun, or easy to do in a large, distributed environment. Organizations typically start off with a project that identifies all (or most) assets at a given point in time but then lose sight of the overall objective and shift resources to support other business priorities. Without continued focus and prioritization of asset management from leadership, the program will ultimately fail.
Budget
IT teams are focused on enabling an ever-changing business and ensuring 99.999% up-time for all systems. As a result, budgets are primarily geared toward operations and capital projects rather than towards asset management.
Process
While most organizations have asset management policies and procedures in place, there is a lack of follow-through of the program due to competing priorities and budgets. Without a strong process, the ability to be effective with asset management becomes increasingly difficult.
The order of these key reasons is important because each one is interconnected in determining success. As always, the impact of “Tone at The Top” will be the ultimate driving factor in the success or failure of a given project.
The Risks Of An Ineffective Asset Management Program
Increased Cost
While there is a cost to effective asset management, organizations without a program will have increased cost from technology licensing. This is most prominent in the applications being used by the general workforce, such as Microsoft 365 and Adobe Acrobat.
Compliance Standards
Many industries are required to comply with specific standards related to privacy and data management, such as HIPAA (healthcare), COPPA (children) and FERPA (students).
However, these standards are ever-evolving and the ability to comply is directly related to having consistent baseline protocols and compliance documentation standards, and then managing assets accordingly.
Lack of Visibility
A lack of visibility poses a risk to IT Ops and Cyber teams alike. While the difference is supportability vs. security monitoring, the overall risk to business disruption is similar in nature.
Lack of visibility could result in the disruption of critical applications and lack of team awareness, thus increasing the overall impact of the outage or inability to determine the root cause to reduce future disruption.
Unplanned Outages
Unmanaged assets lead to unplanned outages. End-of-life assets are at risk of failure leading to business disruption.
Increased Attack Surface
With a lack of asset visibility, organizations are unknowingly increasing their attack surface (aka a “vector”). An attack surface is a point of entry where a threat actor (“hacker”) could gain unauthorized access.
Unmanaged devices increase this risk as applications and operating systems are not patched, monitored, or calculated into the overall risk management program.
Additionally, unmanaged devices are known vectors for threat actors to use to compromise a network.
Getting Started: Effective Asset Management
Now that we’ve outlined the risks, let’s look at how to build an effective asset management program.
An effective program involves technology, people, and processes.
Technology Asset Management
Technology is highly recommended for managing assets within an environment, but the most critical aspect is reconciling asset records to ensure their overall relevance.
Depending on the size and complexity of your organization, you may consider:
- Vulnerability Scanners: dynamic scanning allows for security professionals to identify possibly rouge or unmanaged devices.
- Active Directory / Dynamic Host Configuration Protocol (AD/DHCP): this can be a great source for devices tied to the domain and managed by IT Ops.
- Antivirus Tools: depending on the tool, an AV solution has a discovery mode that allows organizations to identify rogue devices.
- Configuration Management Database (CMDB): the purpose of a CMDB is to store all data about assets and help manage them against contracts, lifecycle management, and overall device purpose.
- Governance: to ensure processes and policies are being followed, a governance model should be implemented to monitor effectiveness.
- Service Management: similar to AD/DHCP, a service management tool will provide data on the assets that are managed by the IT Ops team.
Security Information and Event Management (SIEM): as a data aggregator, the SIEM has the ability to pull all data sources together and custom reporting can be developed to determine what devices are not managed.
People
To have an effective program, leaders must invest in a person or team to manage the end-to-end process.
Asset management requires multiple teams to support the overall program. For larger organizations, the best practice is to have a team responsible for life cycle management of all assets in the environment, rather than assigning to a single IT admin or engineer. This team has responsibility for vendor management, procurement, and project management. It also has a purview on upcoming projects that can identify new devices required.
For small and medium businesses, the person will more than likely have full-time responsibility but some time each week or month should be allocated to updating an asset tracker.
The traditional party responsible for managing assets is IT, but there is an increasing number of Cyber leaders stepping up to take responsibility for asset management. This is due to the overwhelming impacts asset management has on their program.
Processes
Regardless of organization size, the need for a documented and followed process is imperative to the success of the program. The process should consist of validating various sources and following up with owners to ensure relevance of the system or application. (Value Add: This process can reduce unused assets, which can drive cost reduction.)
By leveraging Capability Maturity Model integration (CMMi), which breaks maturity down into five levels, an organization can assess their asset maturity.
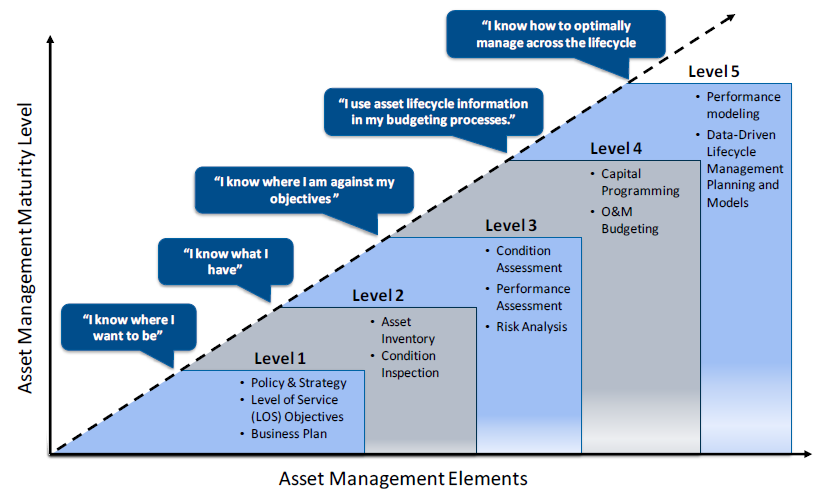
Graphic: Copyright 2013 The Institute of Asset Management
Security Configuration Management
Security configuration management is a critical component of any asset discovery and management strategy.
Organizations have to make sure that all of their IT systems are configured correctly and that any changes to their tools and settings are monitored and managed accordingly. This includes:
- Patching, hardening, and logging configurations
- Updating user accounts, authentication requirements, and access control systems
- Reviewing administrator permissions within all tools and services
Security configuration management can help organizations detect any unusual activity or unauthorized changes to their systems. Security analysts can detect and remediate any potential threats quickly and accurately only when their tools are properly configured.
Furthermore, security configuration management is important for keeping organizations compliant with any applicable industry or government regulations.
Final Thoughts
Asset discovery and management are important preventative measures for cybersecurity, leading to decreased costs, decreased risk, and increased business performance.
However, IT organizations struggle with asset management due to lack of priority, budget, and process. Without an effective asset management program, organizations face a number of risks such as increased cost, compliance issues, lack of visibility, unplanned outages, and increased attack surface.
If you’d like assistance with setting up your organization’s asset discovery and management program, contact Pareto Cyber today.






